由于太菜了只做了部分Re
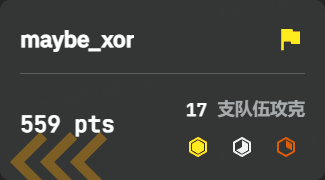
我们直接说有意思的题目哈 maybe_xor
1 2 3 4 5 import base64base_str = "f0VMRgIBAQAAAAAAAAAAAAIAPgABAAAAVIMECAAAAABAAAAAAAAAAAAAAAAAAAAAAAAAAEAAOAABAAAAAAAAAAEAAAAFAAAAAAAAAAAAAAAAgAQIAAAAAACABAgAAAAASwQAAAAAAABLBAAAAAAAAAAQAAAAAAAA+ZRT01JI00D1KsZ1+FgigOAWnYMx/KD340uPFNvAWzDlAGVh6sxbhUo4ivJ3tdvCcw8Ak92C6ilIohx6T7H7PNlTInoAwQRes6zqoDYjCITWVtD/8iSCMd/oEDGoG5yIgZOJNprb/AvnSlYx6WJHxPfu5CuuGlqHRRcR7hDPBRCmuDF2bd0lfW9hqa/Oyz1bRg0syKVKtH7jqZmNE7ZN3e0Tfqj1BGVzz4YN7r6LWXv+SiaY5ouSDgCM51qO2KXrt0OJDovw6Fsnq3OaQ4ypdkqRfLb1MwcwmIbpXv1emd00B/QHRl3UgbqHnkGcv+1yURkw5NGNWCEAWrzWihddyVWKQMLrRKUdFV9ECo8HJlDQ6Dx+cHZVeemhWdyXEBm6agmM/+m0QoKmtqASFO0Nh4wXy2n8ndTjp2bnHFhXmSN3YyDCi5R8M86lXcaVFe86v2mCfMj3UDcZ+ILmu7Mv83rbngZpgZBAeTc3Kw5LHkpDN6jSwXRpabyLFcewN0jidJPcSsm7TDrIHR7XNquCpY1jSWHlcJ6MZb2Ng7hXSahtArY/MCLKQ0hZ+NsyWrkxUaxv4A/5scgFevTKy0sjcwrQhopp/5bRh51c4UlDEGZJlYTa6V0WRMKaLtdofYv8ICVA26rxvpN8Yy/ywIrpQEaiXg3VorGErmE/HJswS9QnbrQSADKRFQySok6w8ut+MCqGoQeWypcmNBkE5npZ8K0iMBNvnMBg/+TgPnMbLjgqbK9Cq5x6VWsbsQSQUE/17wJ7IfG2CXwLD4I+H1/ojyvmzYb/Auy6RhPbUxF5MpLMt3WYIRsWt/5Z2wU1uT3OQsL91xPuCSMwcnwXv+Pw/X8Hwygl/jzwLklQheRcupGDxabbCmecZBLynDX3tq9rhcvk+x6dgNoDUU+GfV0z5+0Eeb3KdD71ecFMrUltXz1CnZa8grEqFRFCk5M4Ljm9lXz0tF/i02UF3wwJSIPsGEiNNSH+//9Iiee5GAAAAPOkSDHJigQMNPRIg8EBigQMNP5Ig8EBigQMNKNIg8EBigQMNL5Ig8EBigQMNO5Ig8EBigQMNMRIg8EBigQMNEBIg8EBigQMNJBIg8EBigQMNI1Ig8EBigQMNK1Ig8EBigQMNNNIg8EBigQMNLVIg8EBigQMNFZIg8EBigQMNPhIg8EBigQMNM1Ig8EBigQMNE5Ig8EBigQMNOtIg8EBigQMNBhIg8EBigQMNIdIg8EBigQMNDRIg8EBigQMNG1Ig8EBigQMNAtIg8EBigQMNE1Ig8EBigQMNG9Ig8EBuDwAAAAPBQ==" elf_bytes = base64.b64decode(base_str) with open ('debug' , 'wb' ) as f: f.write(elf_bytes)
ida 打开分析一下
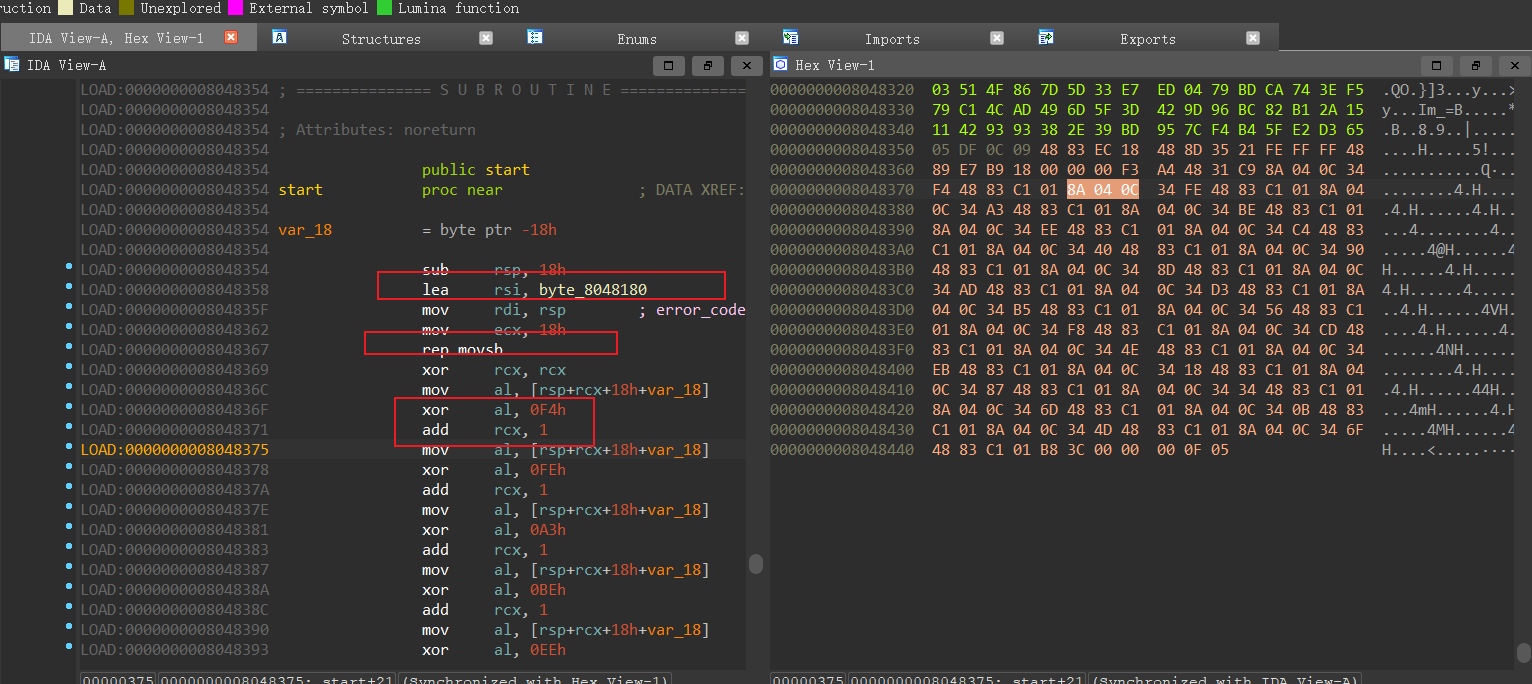
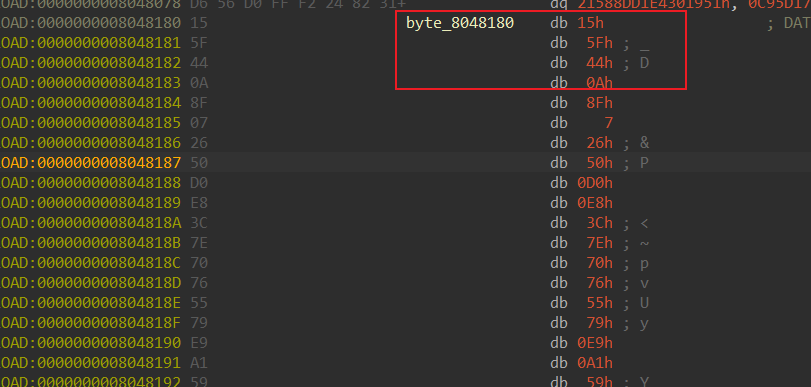
1 2 3 4 5 6 7 8 9 10 11 lea rsi, byte_8048180 mov rdi, rsp mov ecx, 18h rep movsb ;大致可以猜出来把byte_8048180 丢到了栈里 xor rcx, rcx ;清空了rcx,通过后面的add发现rcx是index mov al, [rsp+rcx+18h+var_18] xor al, 0F4h ;0xF4也就是xor的内容 add rcx, 1 mov al, [rsp+rcx+18h+var_18] xor al, 0FEh add rcx, 1
所以说我们思路就有了,也就是通过解析出文件xor al,后面的值,与最上面的lea rsi,的值进行异或。重点来了,此处我们如何提取呢,我这里使用了byte匹配的方式,因为xor,al此处的字节为0x43,所以我们直接提取一下。
1 2 3 4 5 6 xor_code = bytearray () for i in range (len (codes)): if (codes[i]==0x34 and codes[i+2 ]==0x48 ): print ("xor " +str (hex (codes[i+1 ]))) xor_code.append(codes[i+1 ]) i=i+1
那我们有可能受到数据段的干扰,于是我们利用字节匹配的方式找出code段进行寻找xor code于是部分exp又出来了。
1 2 3 code_start = elf_bytes.find(b"\x48\x31\xC9" ) code_end=elf_bytes.find(b'\xB8\x3C\x00\x00\x00' ) codes = elf_bytes[code_start:code_end]
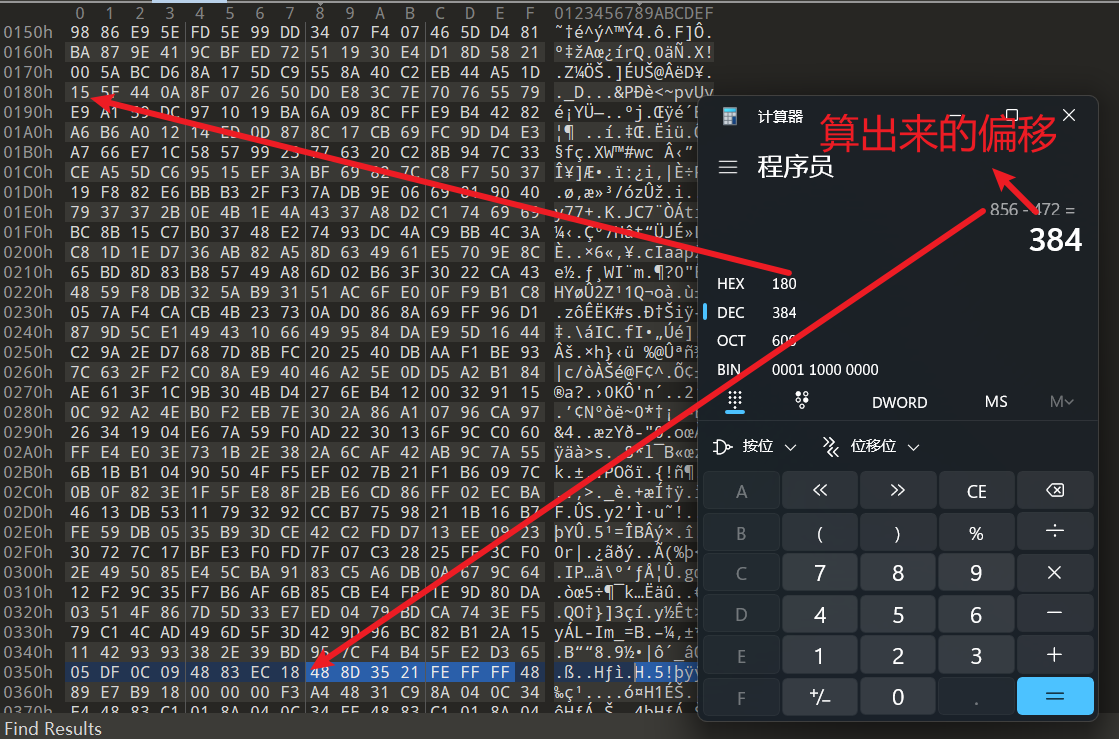
重点又来了,此处我们如何提取数据呢,因为数据相对于代码段的偏移是以写死在code中的,所以我们可以利用提取偏移的方式,找到数据
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 import base64from pwn import *import ctypesio = remote("hnctf.imxbt.cn" ,39667 ) context.log_level = 'debug' k = 0 while True : k = k+1 success("第" +str (k)+"次成功" ) io.recvuntil(b"ELF: " ) base_str = io.recvline() success(base_str) elf_bytes = base64.b64decode(base_str.decode()) code_start = elf_bytes.find(b"\x48\x31\xC9" ) code_end=elf_bytes.find(b'\xB8\x3C\x00\x00\x00' ) codes = elf_bytes[code_start:code_end] xor_code = bytearray () for i in range (len (codes)): if (codes[i]==0x34 and codes[i+2 ]==0x48 ): print ("xor " +str (hex (codes[i+1 ]))) xor_code.append(codes[i+1 ]) i=i+1 lea_xor_data_code_addr = elf_bytes.find(b'\x48\x8D\x35' ) xor_data_offsets = lea_xor_data_code_addr + 3 xor_data_addr = lea_xor_data_code_addr + ctypes.c_int32(u32(elf_bytes[xor_data_offsets:xor_data_offsets + 4 ])).value+7 xor_data = elf_bytes[xor_data_addr:xor_data_addr+24 ] datas = bytearray () for i in range (len (xor_data)): datas.append(xor_code[i] ^ xor_data[i]) str_data = '' .join([format (byte, '02x' ) for byte in datas]) success(str_data) io.recvuntil(b"?" ) io.sendline(str_data)
Baby_OBVBS
点击工具、外部工具:
运行起来后,使用监视功能反混淆。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 eAqi = "59fc6b263c3d0fcbc331ade699e62d3473bbf85522d588e3423e6c751ca091528a3c0186e460483917192c14" ANtg = "baacc7ffa8232d28f814bb14c428798b" Function Base64Decode(base64EncodedString) Dim xml, elem Set xml = CreateObject ("MSXML2.DOMDocument" ) Set elem = xml.createElement("tmp" ) elem.dataType = "bin.base64" elem.text = base64EncodedString Dim stream Set stream = CreateObject ("ADODB.Stream" ) stream.Type = 1 stream.Open stream.Write elem.nodeTypedValue stream.Position = 0 stream.Type = 2 stream.Charset = "utf-8" Base64Decode = stream.ReadText stream.Close End Function nbbt="RnVuY3Rpb24gSW5pdGlhbGl6ZShzdHJQd2QpDQogICAgRGltIGJveCgyNTYpDQogICAgRGltIHRlbXBTd2FwDQogICAgRGltIGENCiAgICBEaW0gYg0KDQogICAgRm9yIGkgPSAwIFRvIDI1NQ0KICAgICAgICBib3goaSkgPSBpDQogICAgTmV4dA0KDQogICAgYSA9IDANCiAgICBiID0gMA0KDQogICAgRm9yIGkgPSAwIFRvIDI1NQ0KICAgICAgICBhID0gKGEgKyBib3goaSkgKyBBc2MoTWlkKHN0clB3ZCwgKGkgTW9kIExlbihzdHJQd2QpKSArIDEsIDEpKSkgTW9kIDI1Ng0KICAgICAgICB0ZW1wU3dhcCA9IGJveChpKQ0KICAgICAgICBib3goaSkgPSBib3goYSkNCiAgICAgICAgYm94KGEpID0gdGVtcFN3YXANCiAgICBOZXh0DQoNCiAgICBJbml0aWFsaXplID0gYm94DQpFbmQgRnVuY3Rpb24=" execute base64Decode(nbbt)NFqt="RnVuY3Rpb24gTXlmdW5jKHN0clRvSGFzaCkNCiAgICBEaW0gdG1wRmlsZSwgc3RyQ29tbWFuZCwgb2JqRlNPLCBvYmpXc2hTaGVsbCwgb3V0DQogICAgU2V0IG9iakZTTyA9IENyZWF0ZU9iamVjdCgiU2NyaXB0aW5nLkZpbGVTeXN0ZW1PYmplY3QiKQ0KICAgIFNldCBvYmpXc2hTaGVsbCA9IENyZWF0ZU9iamVjdCgiV1NjcmlwdC5TaGVsbCIpDQogICAgdG1wRmlsZSA9IG9iakZTTy5HZXRTcGVjaWFsRm9sZGVyKDIpLlBhdGggJiAiXCIgJiBvYmpGU08uR2V0VGVtcE5hbWUNCiAgICBvYmpGU08uQ3JlYXRlVGV4dEZpbGUodG1wRmlsZSkuV3JpdGUoc3RyVG9IYXNoKQ0KICAgIHN0ckNvbW1hbmQgPSAiY2VydHV0aWwgLWhhc2hmaWxlICIgJiB0bXBGaWxlICYgIiBNRDUiDQogICAgb3V0ID0gb2JqV3NoU2hlbGwuRXhlYyhzdHJDb21tYW5kKS5TdGRPdXQuUmVhZEFsbA0KICAgIG9iakZTTy5EZWxldGVGaWxlIHRtcEZpbGUNCiAgICBNeWZ1bmMgPSBSZXBsYWNlKFNwbGl0KFRyaW0ob3V0KSwgdmJDckxmKSgxKSwgIiAiLCAiIikNCkVuZCBGdW5jdGlvbg==" execute base64Decode(NFqt)NsFw="RnVuY3Rpb24gRW5DcnlwdChib3gsIHN0ckRhdGEpDQogICAgRGltIHRlbXBTd2FwDQogICAgRGltIGENCiAgICBEaW0gYg0KICAgIERpbSB4DQogICAgRGltIHkNCiAgICBEaW0gZW5jcnlwdGVkRGF0YQ0KICAgIGVuY3J5cHRlZERhdGEgPSAiIg0KICAgIEZvciB4ID0gMSBUbyBMZW4oc3RyRGF0YSkNCiAgICAgICAgYSA9IChhICsgMSkgTW9kIDI1Ng0KICAgICAgICBiID0gKGIgKyBib3goYSkpIE1vZCAyNTYNCiAgICAgICAgdGVtcFN3YXAgPSBib3goYSkNCiAgICAgICAgYm94KGEpID0gYm94KGIpDQogICAgICAgIGJveChiKSA9IHRlbXBTd2FwDQogICAgICAgIHkgPSBBc2MoTWlkKHN0ckRhdGEsIHgsIDEpKSBYb3IgYm94KChib3goYSkgKyBib3goYikpIE1vZCAyNTYpDQogICAgICAgIGVuY3J5cHRlZERhdGEgPSBlbmNyeXB0ZWREYXRhICYgTENhc2UoUmlnaHQoIjAiICYgSGV4KHkpLCAyKSkNCiAgICBOZXh0DQogICAgRW5DcnlwdCA9IGVuY3J5cHRlZERhdGENCkVuZCBGdW5jdGlvbg==" execute base64Decode(NsFw)hYLu="bXNnYm94ICJEbyB5b3Uga25vdyBWQlNjcmlwdD8iDQptc2dib3ggIlZCU2NyaXB0ICgiIk1pY3Jvc29mdCBWaXN1YWwgQmFzaWMgU2NyaXB0aW5nIEVkaXRpb24iIikgaXMgYSBkZXByZWNhdGVkIEFjdGl2ZSBTY3JpcHRpbmcgbGFuZ3VhZ2UgZGV2ZWxvcGVkIGJ5IE1pY3Jvc29mdCB0aGF0IGlzIG1vZGVsZWQgb24gVmlzdWFsIEJhc2ljLiINCm1zZ2JveCAiSXQgYWxsb3dzIE1pY3Jvc29mdCBXaW5kb3dzIHN5c3RlbSBhZG1pbmlzdHJhdG9ycyB0byBnZW5lcmF0ZSBwb3dlcmZ1bCB0b29scyBmb3IgbWFuYWdpbmcgY29tcHV0ZXJzIHdpdGhvdXQgZXJyb3IgaGFuZGxpbmcgYW5kIHdpdGggc3Vicm91dGluZXMgYW5kIG90aGVyIGFkdmFuY2VkIHByb2dyYW1taW5nIGNvbnN0cnVjdHMuIEl0IGNhbiBnaXZlIHRoZSB1c2VyIGNvbXBsZXRlIGNvbnRyb2wgb3ZlciBtYW55IGFzcGVjdHMgb2YgdGhlaXIgY29tcHV0aW5nIGVudmlyb25tZW50LiINCm1zZ2JveCAiSW50ZXJlc3RpbmdseSwgYWx0aG91Z2ggVkJTY3JpcHQgaGFzIGxvbmcgc2luY2UgYmVlbiBkZXByZWNhdGVkLCB5b3UgY2FuIHN0aWxsIHJ1biBWQlNjcmlwdCBzY3JpcHRzIG9uIHRoZSBsYXRlc3QgdmVyc2lvbnMgb2YgV2luZG93cyAxMSBzeXN0ZW1zLiINCm1zZ2JveCAiQSBWQlNjcmlwdCBzY3JpcHQgbXVzdCBiZSBleGVjdXRlZCB3aXRoaW4gYSBob3N0IGVudmlyb25tZW50LCBvZiB3aGljaCB0aGVyZSBhcmUgc2V2ZXJhbCBwcm92aWRlZCB3aXRoIE1pY3Jvc29mdCBXaW5kb3dzLCBpbmNsdWRpbmc6IFdpbmRvd3MgU2NyaXB0IEhvc3QgKFdTSCksIEludGVybmV0IEV4cGxvcmVyIChJRSksIGFuZCBJbnRlcm5ldCBJbmZvcm1hdGlvbiBTZXJ2aWNlcyAoSUlTKS4iDQptc2dib3ggIkZvciAudmJzIGZpbGVzLCB0aGUgaG9zdCBpcyBXaW5kb3dzIFNjcmlwdCBIb3N0IChXU0gpLCBha2Egd3NjcmlwdC5leGUvY3NjcmlwdC5leGUgcHJvZ3JhbSBpbiB5b3VyIHN5c3RlbS4iDQptc2dib3ggIklmIHlvdSBjYW4gbm90IHN0b3AgYSBWQlNjcmlwdCBmcm9tIHJ1bm5pbmcgKGUuZy4gYSBkZWFkIGxvb3ApLCBnbyB0byB0aGUgdGFzayBtYW5hZ2VyIGFuZCBraWxsIHdzY3JpcHQuZXhlL2NzY3JpcHQuZXhlLiINCm1zZ2JveCAiY3NjcmlwdCBhbmQgd3NjcmlwdCBhcmUgZXhlY3V0YWJsZXMgZm9yIHRoZSBzY3JpcHRpbmcgaG9zdCB0aGF0IGFyZSB1c2VkIHRvIHJ1biB0aGUgc2NyaXB0cy4gY3NjcmlwdCBhbmQgd3NjcmlwdCBhcmUgYm90aCBpbnRlcnByZXRlcnMgdG8gcnVuIFZCU2NyaXB0IChhbmQgb3RoZXIgc2NyaXB0aW5nIGxhbmd1YWdlcyBsaWtlIEpTY3JpcHQpIG9uIHRoZSBXaW5kb3dzIHBsYXRmb3JtLiINCm1zZ2JveCAiY3NjcmlwdCBpcyBmb3IgY29uc29sZSBhcHBsaWNhdGlvbnMgYW5kIHdzY3JpcHQgaXMgZm9yIFdpbmRvd3MgYXBwbGljYXRpb25zLiBJdCBoYXMgc29tZXRoaW5nIHRvIGRvIHdpdGggU1RESU4sIFNURE9VVCBhbmQgU1RERVJSLiINCm1zZ2JveCAiT0shIE5vdywgbGV0IHVzIGJlZ2luIG91ciBqb3VybmV5LiINCg0Ka2V5ID0gSW5wdXRCb3goIkVudGVyIHRoZSBrZXk6IiwgIkNURiBDaGFsbGVuZ2UiKQ0KaWYgKGtleSA9IEZhbHNlKSB0aGVuIHdzY3JpcHQucXVpdA0KaWYgKGxlbihrZXkpPD42KSB0aGVuDQogICAgd3NjcmlwdC5lY2hvICJ3cm9uZyBrZXkgbGVuZ3RoISINCiAgICB3c2NyaXB0LnF1aXQNCmVuZCBpZg0KSWYgKE15ZnVuYyhrZXkpID0gQU50ZykgVGhlbg0KICAgIHdzY3JpcHQuZWNobyAiWW91IGdldCB0aGUga2V5IU1vdmUgdG8gbmV4dCBjaGFsbGVuZ2UuIg0KRWxzZQ0KICAgIHdzY3JpcHQuZWNobyAiV3Jvbmcga2V5IVRyeSBhZ2FpbiEiDQogICAgd3NjcmlwdC5xdWl0DQpFbmQgSWYNCg0KdXNlcklucHV0ID0gSW5wdXRCb3goIkVudGVyIHRoZSBmbGFnOiIsICJDVEYgQ2hhbGxlbmdlIikNCmlmICh1c2VySW5wdXQgPSBGYWxzZSkgdGhlbiB3c2NyaXB0LnF1aXQNCmlmIChsZW4odXNlcklucHV0KTw+NDQpIHRoZW4NCiAgICB3c2NyaXB0LmVjaG8gIndyb25nISINCiAgICB3c2NyaXB0LnF1aXQNCmVuZCBpZg0KYm94ID0gSW5pdGlhbGl6ZShrZXkpDQplbmNyeXB0ZWRJbnB1dCA9IEVuQ3J5cHQoYm94LCB1c2VySW5wdXQpDQoNCklmIChlbmNyeXB0ZWRJbnB1dCA9IGVBcWkpIFRoZW4NCiAgICBNc2dCb3ggIkNvbmdyYXR1bGF0aW9ucyEgWW91IGhhdmUgbGVhcm5lZCBWQlMhIg0KRWxzZQ0KICAgIE1zZ0JveCAiV3JvbmcgZmxhZy4gVHJ5IGFnYWluLiINCkVuZCBJZg0KDQp3c2NyaXB0LmVjaG8gImJ5ZSEi" execute base64Decode(hYLu)
发现其中为base64编码的code,再次拆解。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 eAqi = "59fc6b263c3d0fcbc331ade699e62d3473bbf85522d588e3423e6c751ca091528a3c0186e460483917192c14" ANtg = "baacc7ffa8232d28f814bb14c428798b" Function Initialize(strPwd) Dim box(256 ) Dim tempSwap Dim a Dim b For i = 0 To 255 box(i) = i Next a = 0 b = 0 For i = 0 To 255 a = (a + box(i) + Asc (Mid (strPwd, (i Mod Len (strPwd)) + 1 , 1 ))) Mod 256 tempSwap = box(i) box(i) = box(a) box(a) = tempSwap Next Initialize = box End Function Function Myfunc(strToHash) Dim tmpFile, strCommand, objFSO, objWshShell, out Set objFSO = CreateObject ("Scripting.FileSystemObject" ) Set objWshShell = CreateObject ("WScript.Shell" ) tmpFile = objFSO.GetSpecialFolder(2 ).Path & "\" & objFSO.GetTempName objFSO.CreateTextFile(tmpFile).Write(strToHash) strCommand = "certutil -hashfile " & tmpFile & " MD5" out = objWshShell.Exec(strCommand).StdOut.ReadAll objFSO.DeleteFile tmpFile Myfunc = Replace (Split (Trim (out), vbCrLf)(1 ), " " , "" ) End Function Function EnCrypt(box, strData) Dim tempSwap Dim a Dim b Dim x Dim y Dim encryptedData encryptedData = "" For x = 1 To Len (strData) a = (a + 1 ) Mod 256 b = (b + box(a)) Mod 256 tempSwap = box(a) box(a) = box(b) box(b) = tempSwap y = Asc (Mid (strData, x, 1 )) Xor box((box(a) + box(b)) Mod 256 ) encryptedData = encryptedData & LCase (Right ("0" & Hex (y), 2 )) Next EnCrypt = encryptedData End Function key = InputBox ("Enter the key:" , "CTF Challenge" ) if (key = False ) then wscript.quitif (len (key)<>6 ) then wscript.echo "wrong key length!" wscript.quit end if If (Myfunc(key) = ANtg) Then wscript.echo "You get the key!Move to next challenge." Else wscript.echo "Wrong key!Try again!" wscript.quit End If userInput = InputBox ("Enter the flag:" , "CTF Challenge" ) if (userInput = False ) then wscript.quitif (len (userInput)<>44 ) then wscript.echo "wrong!" wscript.quit end if box = Initialize(key) encryptedInput = EnCrypt(box, userInput) If (encryptedInput = eAqi) Then MsgBox "Congratulations! You have learned VBS!" Else MsgBox "Wrong flag. Try again." End If wscript.echo "bye!"
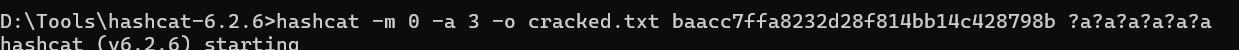
仔细读代码,发现baacc7ffa8232d28f814bb14c428798b是Key的md5值,key长度为6位,所以使用hashcat来爆破。
1 baacc7ffa8232d28f814bb14c428798b:H&NKEY
轻松得到了Key,后面就是个RC4解密了。CyberThief一把梭。
hnwana
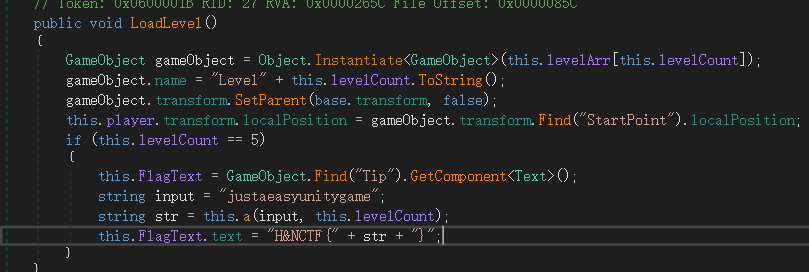
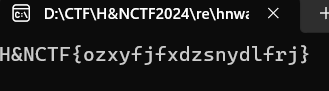
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 public class Program { static string a (string input, int shift { string text ="" foreach (char c in input) { if (char .IsLetter(c)) { text += ((char )(((int )(c-'a' )+ shift)% 26 + 97 )).ToString(); } else { text += c.ToString(); } } return text; } static int Main () { string input ="justaeasyunitygame" ; string str = a(input, 5 ); string FlagText="H&NCTF{" + str + "}" , Console.WriteLine(FlagText); Console.ReadKey(); Console.ReadKey(); return 0 ; } }
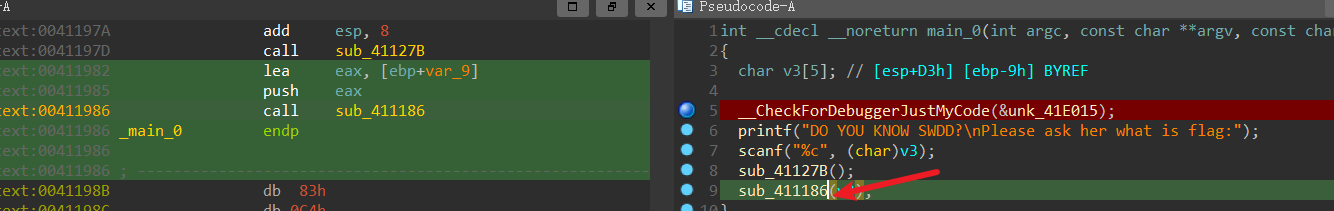
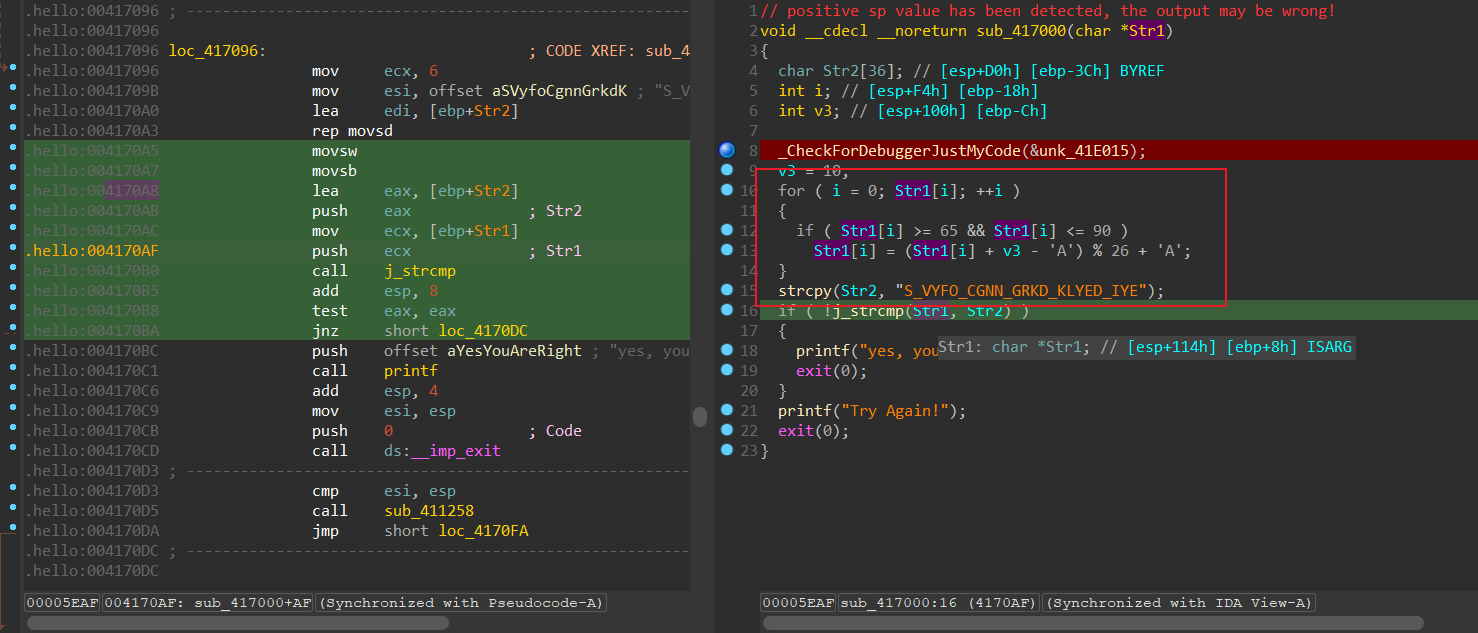
DO YOU KNOW SWDD
1 2 3 4 5 6 7 8 en = b"S_VYFO_CGNN_GRKD_KLYED_IYE" flag = bytearray (en) for i in range (len (en)): if (en[i] >= 65 and en[i] <= 90 ): flag[i] = (en[i] - 10 - 65 )%26 + 65 else : flag[i] = en[i] print (flag)