国城杯wp
Reverse
Crush’s_secret
签到题,SMC+xxtea。
ida随便点点就能看到SMC段
懒得分析解密,直接跑起来,然后dump。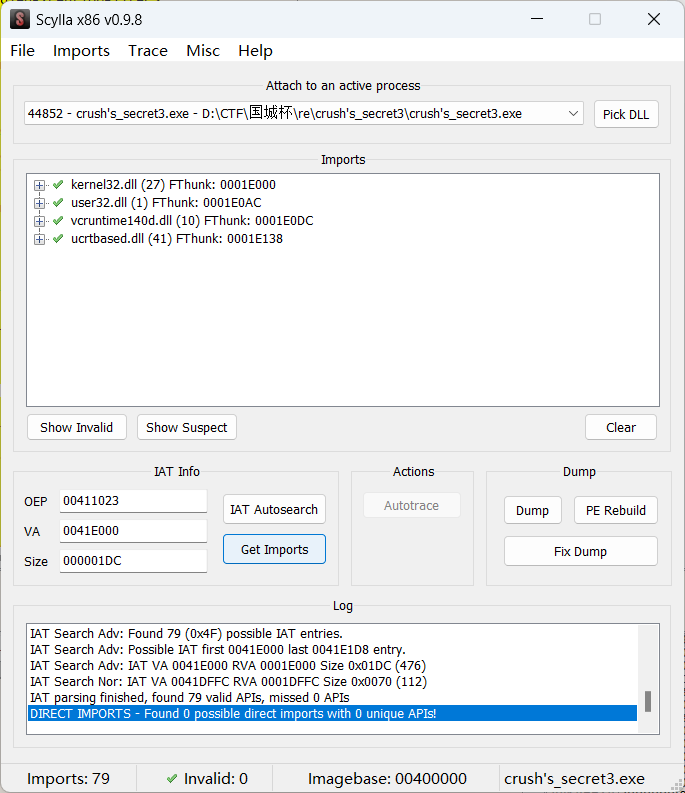
一眼XXTEA,网上的代码,一点没改,直接网上找一个解密就行了。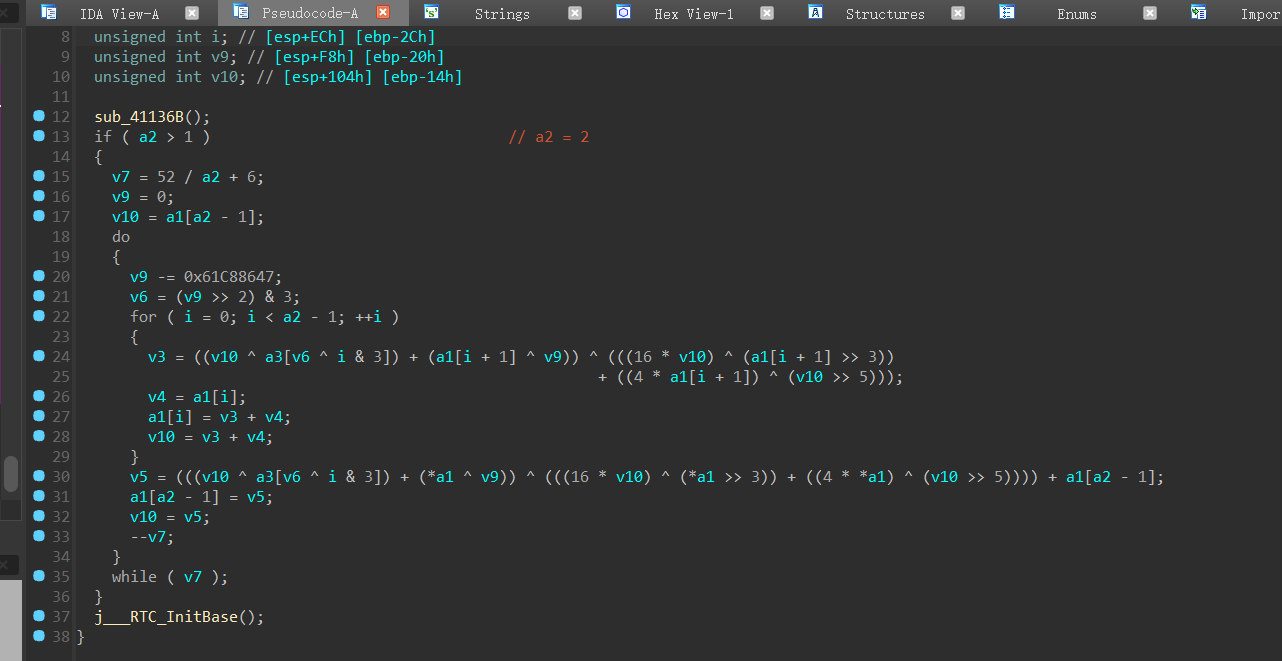
1 |
|
esay_key(easy_key)
题目名字还不太对。不过是驱动题喜欢,但是好像写的有bug按键盘就蓝屏,看起来IRQL处理有点问题
一血不过后面Lilac队在快结束的时候做出来了。
他有个提示就是看看如何交互,直接ida看常见的交互点(Irp包)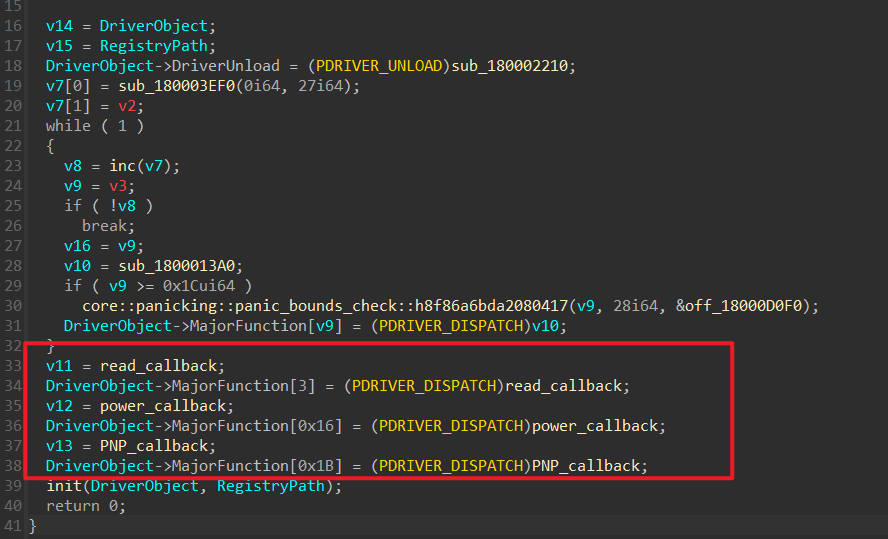
函数入口点可以发现只有IRP_MJ_READ、IRP_MJ_POWER、IRP_MJ_PNP是有点用的,其他的都是个那种默认的派遣函数回调。
后面2我开发的时候没用到,直接看Read。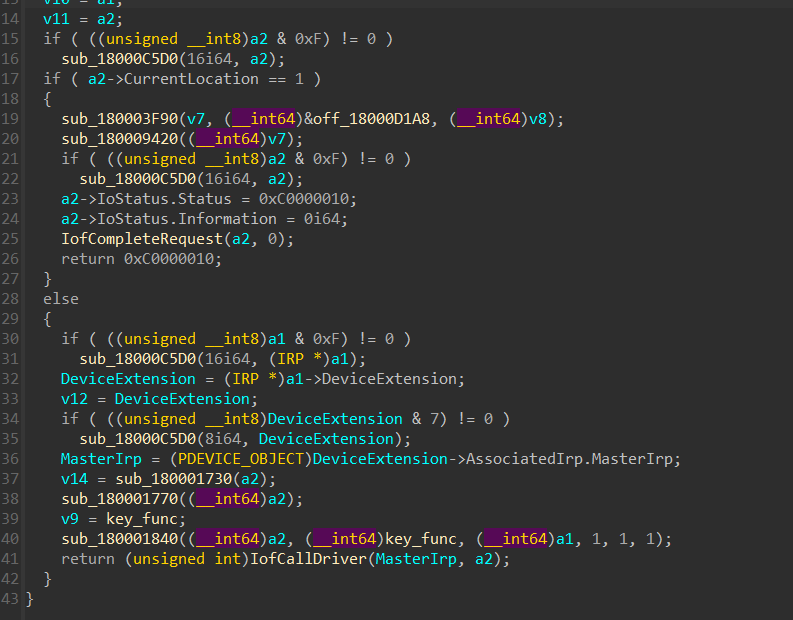
进去看一下发现不太一样,竟然有2段有些可疑。直接把他跑起来拿ARK工具看看情况。打开Windows的测试模式+一个能加载驱动的程序就行(没有的话可以用sc命令创建服务的方式来加载驱动)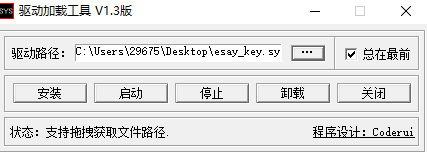
加载进去后用ARK看看他都干了啥,结果发现是个键盘过滤驱动。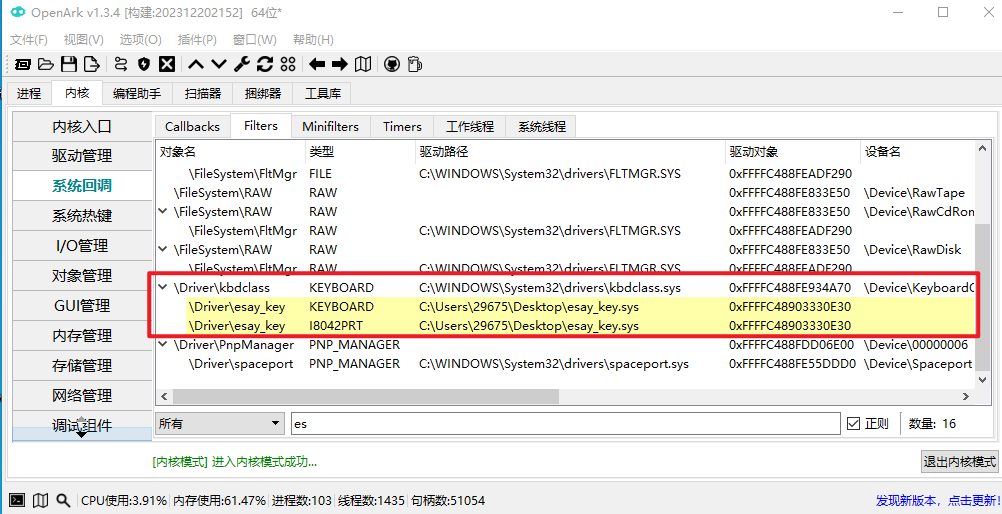
转回ida,我们分析read函数底下那些,点一点就能找到关键函数。
其中这个函数超级长,底下可以发现一个数组,然后还有判断的地方。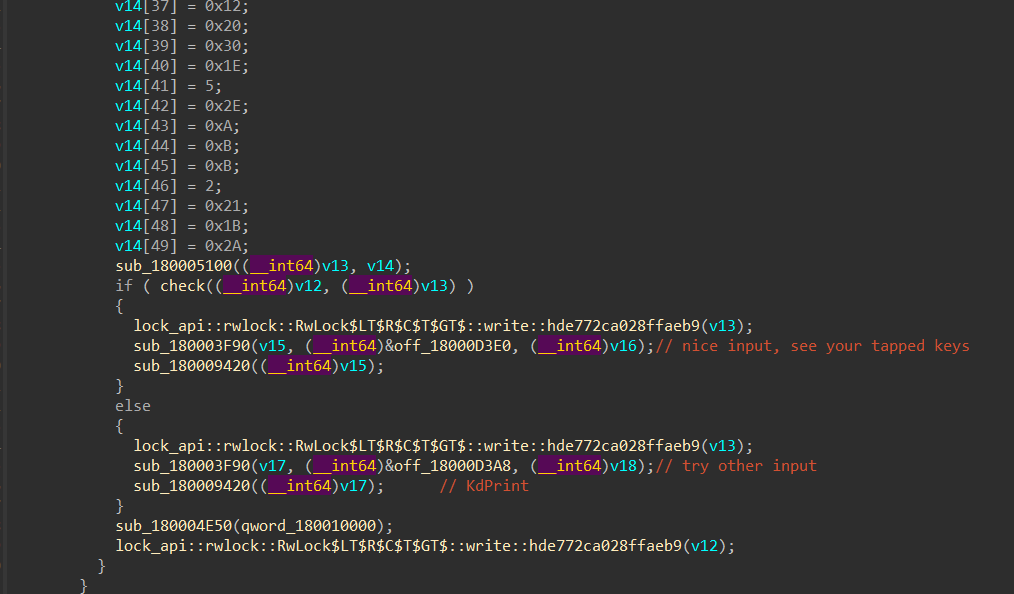
结合ARK的分析就能发现这个是过滤的键盘代码。我也没写过键盘过滤驱动,直接看雪搜一下,就能发现一个教你写键盘驱动的帖子 ,把代码复制下来编译一下就能使用。
按下键盘对着找一下就行了。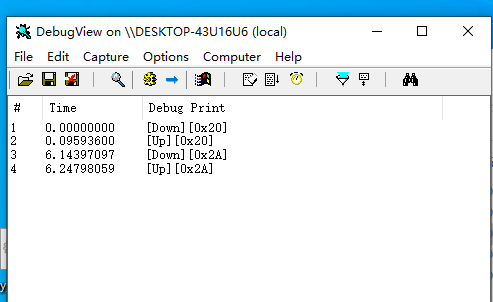
1 | v14[0] = 0x20; D |
round
安卓题,全在java里面,直接jadx看。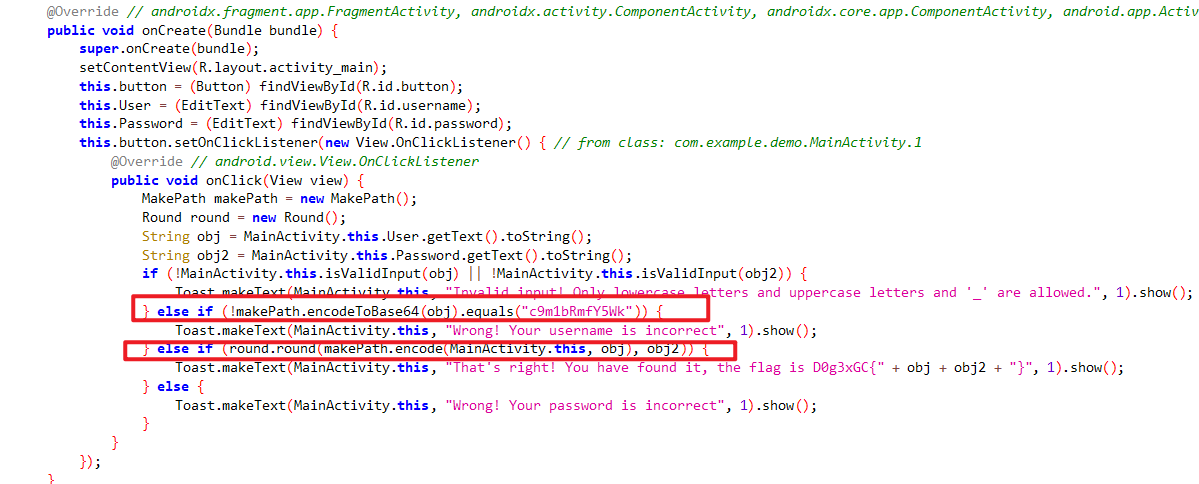
两步,cyber解不了,去看一下b64,不过我没看出来,我直接试了一下,发现其每4个字符一组的中间2个字符会对调。
这里使用frida就能发现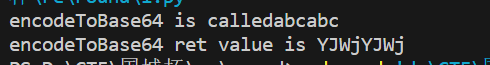
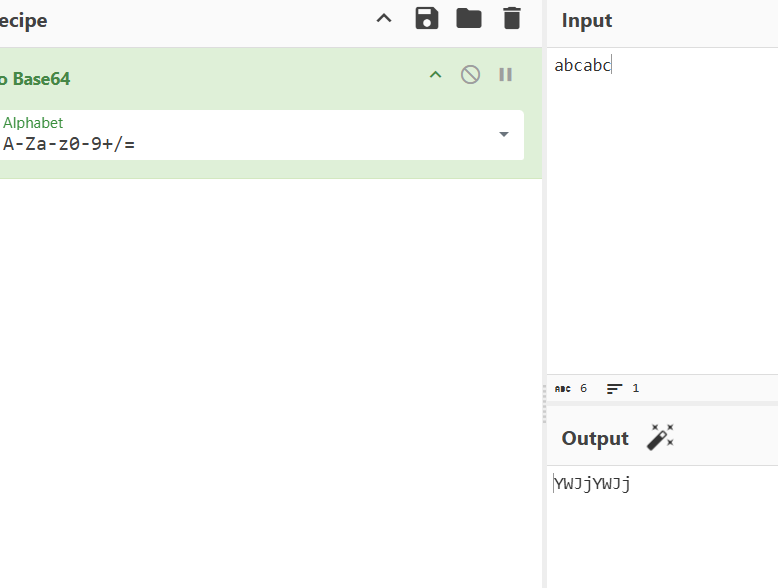
frida代码片段如下:
1 | let MakePath = Java.use("com.example.demo.MakePath"); |
所以直接解密出第一段。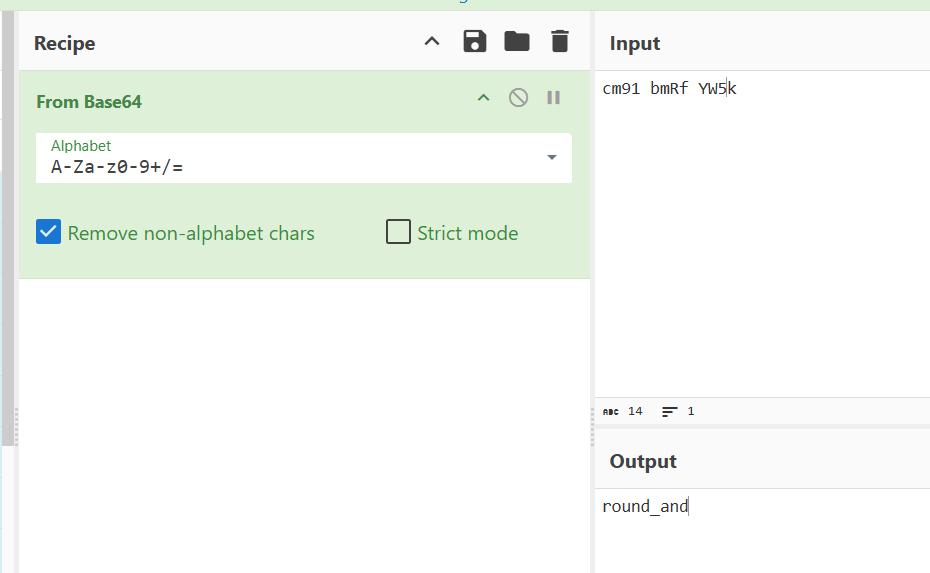
第二段需要一个box,我们可以通过frida直接获得。
完整代码如下
1 | import frida |
至此获得完第二步的所有参数,开始第二步。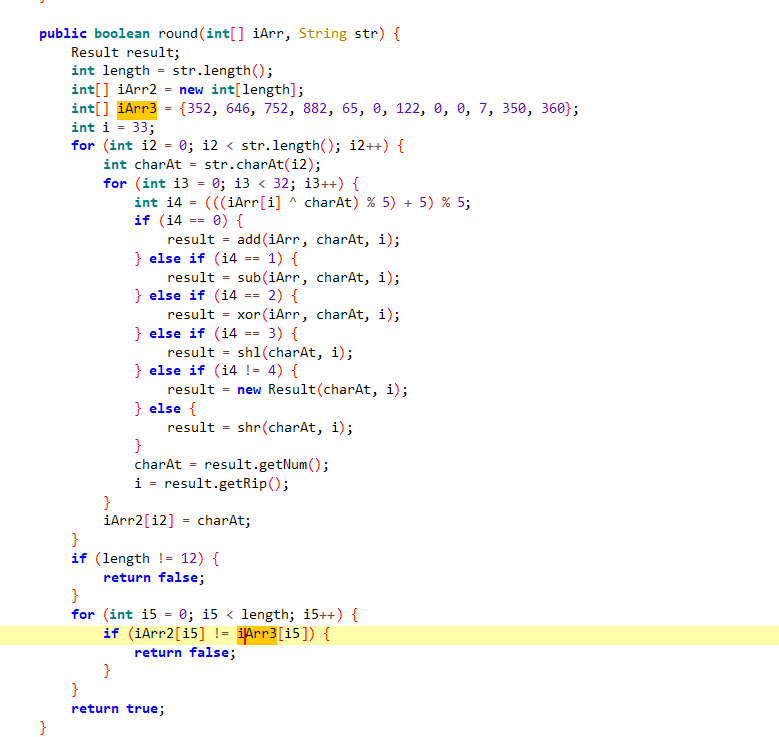
看起来是个很麻烦的算法,直接考虑爆破。
我们把他复制到另一个文件中来执行,我们一开始考虑的就是常规的单字节爆破,但是发现他这个并不是一一对应的,有可能在一个位子上的好几个字符都能对应他这个正确的值,所以我们需要修改爆破代码。
我也不擅长写代码,前面能正常单字节爆破的就是正常爆破,后面的部分爆破方式如下所示:
1 | class Round { |
我们从最后的数据中选择出长度是能到最后一位的就是flag。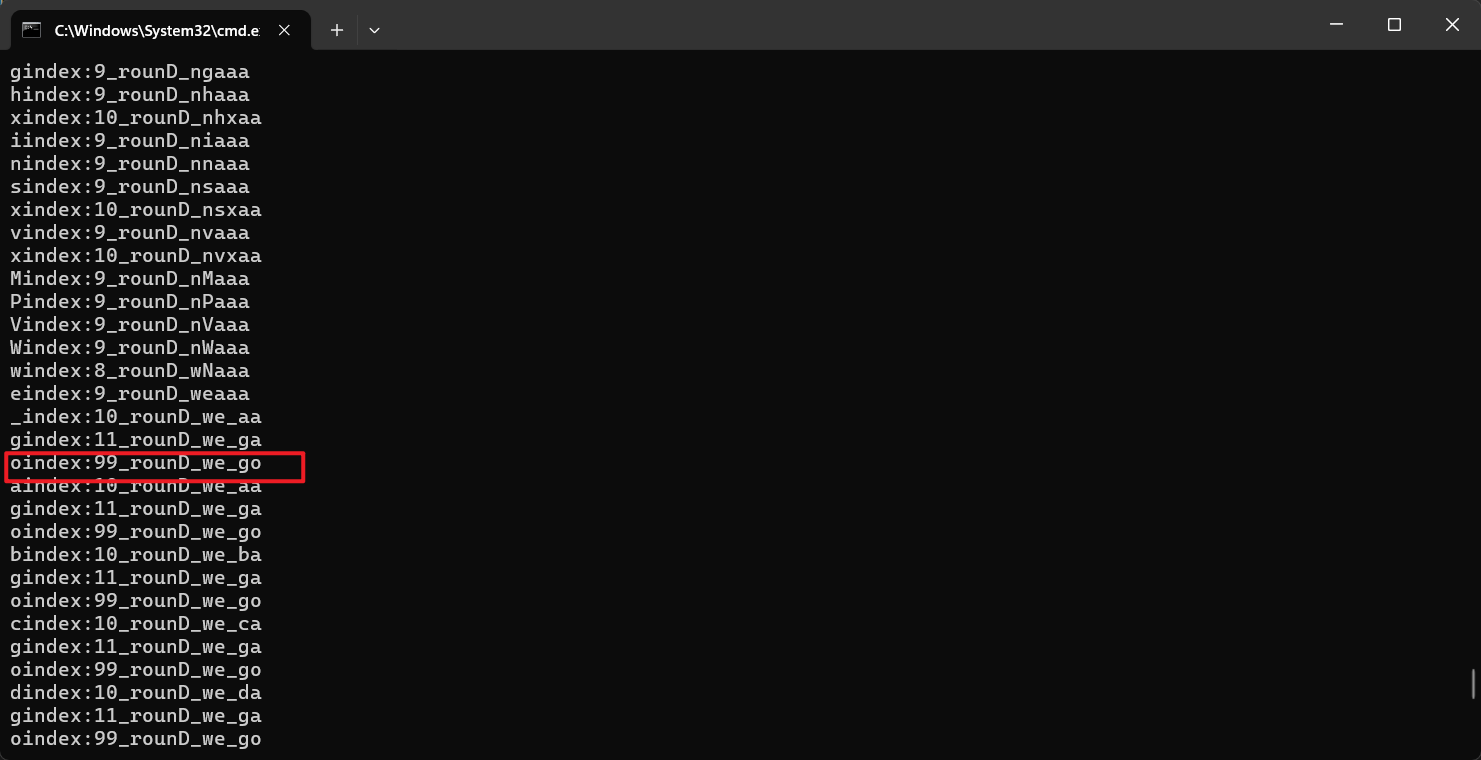
Misc
Tr4ffIc_w1th_Ste90
首先是对流量的处理,打开看到MPEG TS协议。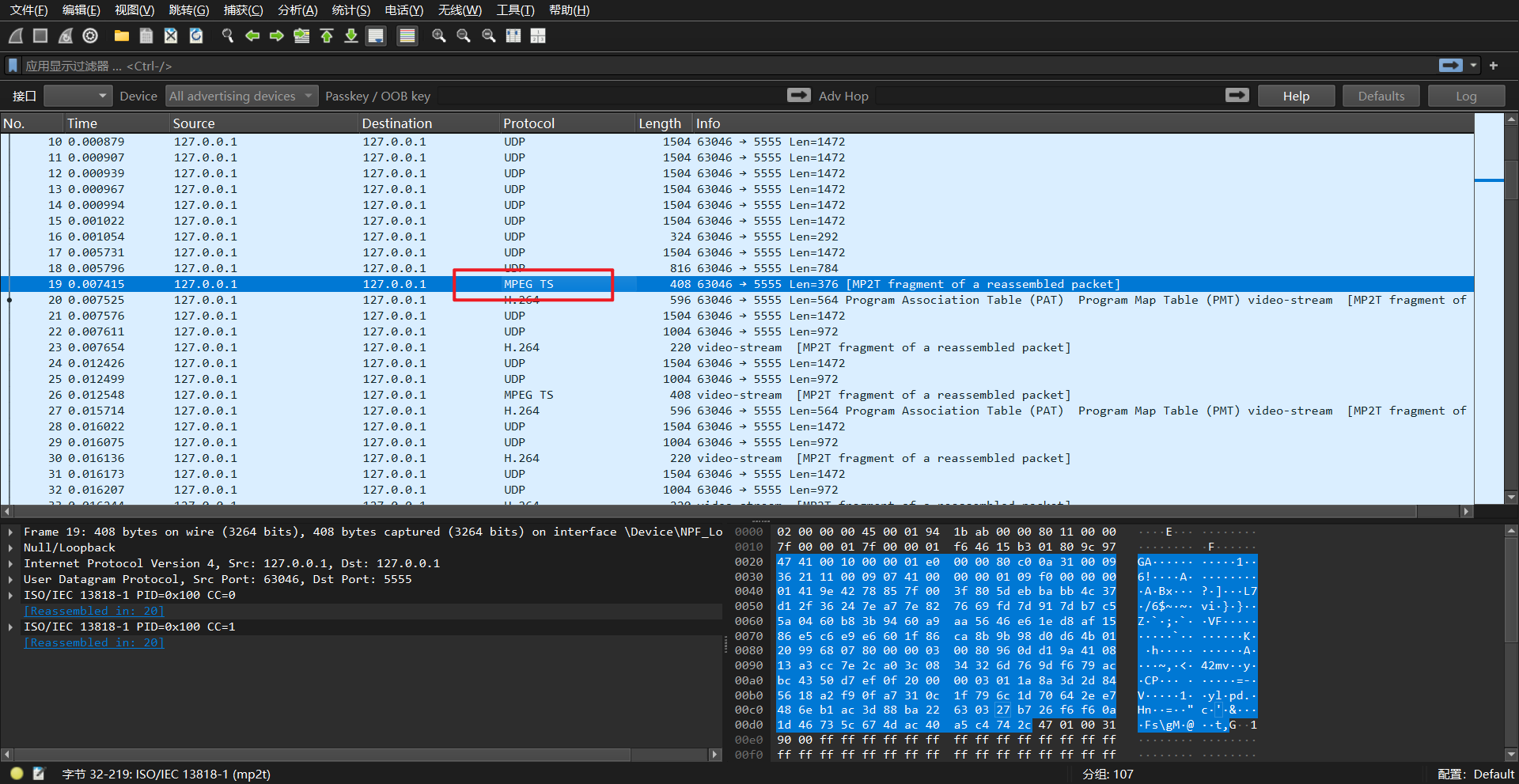
直接追踪流+导出为.ts的视频即可。
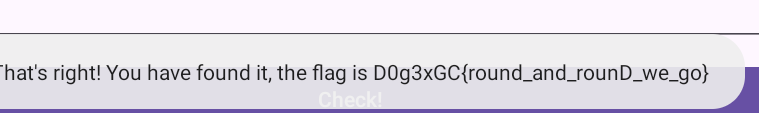
播放即得密码。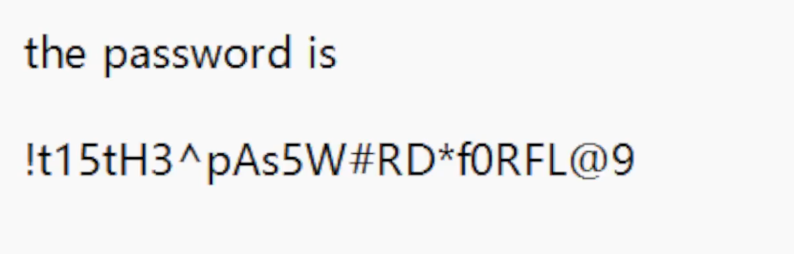
打开发现给了加密图片的脚本,直接让gpt写个解密的即可。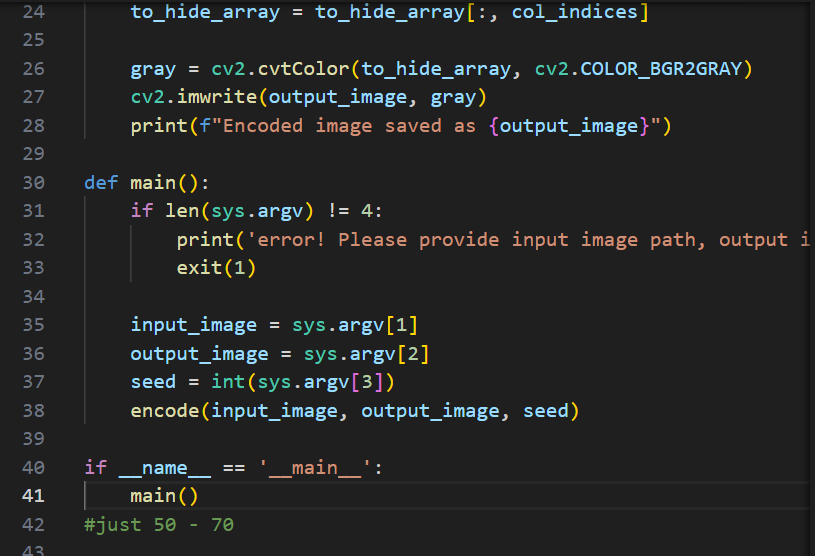
1 | import numpy as np |
然后发现是个Data Matrix码,直接解码就行。
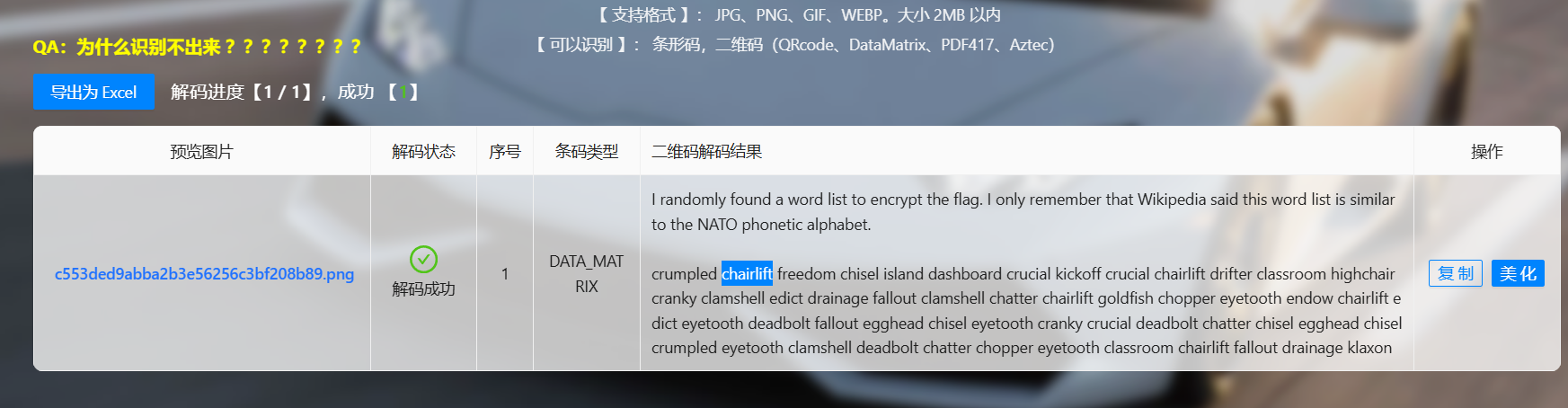
给了一段话。
1 | I randomly found a word list to encrypt the flag. I only remember that Wikipedia said this word list is similar to the NATO phonetic alphabet. |
我们直接提取关键词去维基百科搜索一些就行。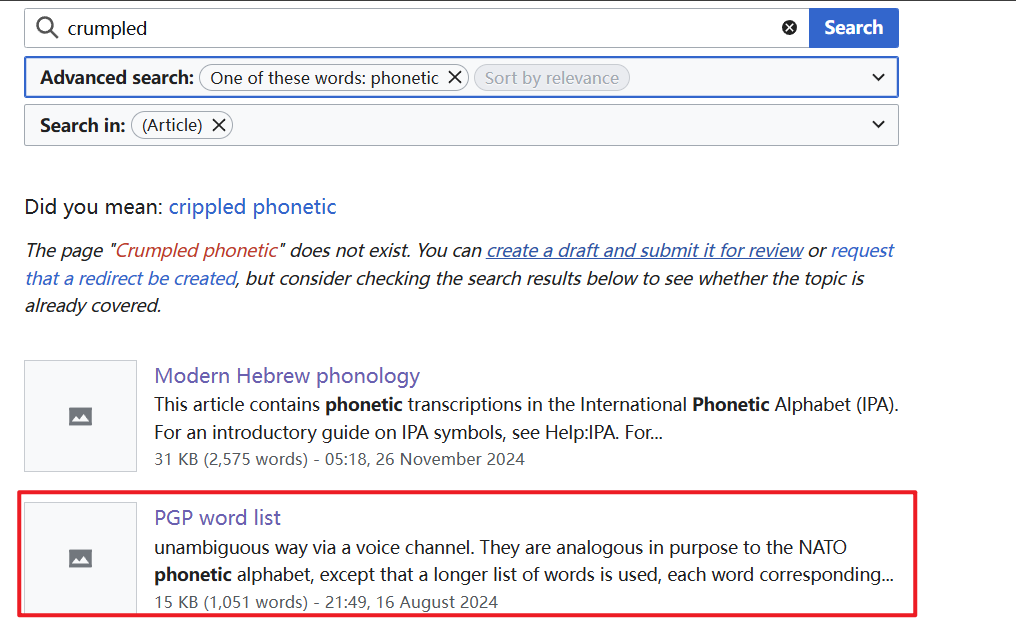
发现是这个PGP word list
直接搓脚本解密就行。
word_list = {
"aardvark": 0x00, "adroitness": 0x00,
"absurd": 0x01, "adviser": 0x01,
"accrue": 0x02, "aftermath": 0x02,
"acme": 0x03, "aggregate": 0x03,
"adrift": 0x04, "alkali": 0x04,
"adult": 0x05, "almighty": 0x05,
"afflict": 0x06, "amulet": 0x06,
"ahead": 0x07, "amusement": 0x07,
"aimless": 0x08, "antenna": 0x08,
"Algol": 0x09, "applicant": 0x09,
"allow": 0x0A, "Apollo": 0x0A,
"alone": 0x0B, "armistice": 0x0B,
"ammo": 0x0C, "article": 0x0C,
"ancient": 0x0D, "asteroid": 0x0D,
"apple": 0x0E, "Atlantic": 0x0E,
"artist": 0x0F, "atmosphere": 0x0F,
"assume": 0x10, "autopsy": 0x10,
"Athens": 0x11, "Babylon": 0x11,
"atlas": 0x12, "backwater": 0x12,
"Aztec": 0x13, "barbecue": 0x13,
"baboon": 0x14, "belowground": 0x14,
"backfield": 0x15, "bifocals": 0x15,
"backward": 0x16, "bodyguard": 0x16,
"banjo": 0x17, "bookseller": 0x17,
"beaming": 0x18, "borderline": 0x18,
"bedlamp": 0x19, "bottomless": 0x19,
"beehive": 0x1A, "Bradbury": 0x1A,
"beeswax": 0x1B, "bravado": 0x1B,
"befriend": 0x1C, "Brazilian": 0x1C,
"Belfast": 0x1D, "breakaway": 0x1D,
"berserk": 0x1E, "Burlington": 0x1E,
"billiard": 0x1F, "businessman": 0x1F,
"bison": 0x20, "butterfat": 0x20,
"blackjack": 0x21, "Camelot": 0x21,
"blockade": 0x22, "candidate": 0x22,
"blowtorch": 0x23, "cannonball": 0x23,
"bluebird": 0x24, "Capricorn": 0x24,
"bombast": 0x25, "caravan": 0x25,
"bookshelf": 0x26, "caretaker": 0x26,
"brackish": 0x27, "celebrate": 0x27,
"breadline": 0x28, "cellulose": 0x28,
"breakup": 0x29, "certify": 0x29,
"brickyard": 0x2A, "chambermaid": 0x2A,
"briefcase": 0x2B, "Cherokee": 0x2B,
"Burbank": 0x2C, "Chicago": 0x2C,
"button": 0x2D, "clergyman": 0x2D,
"buzzard": 0x2E, "coherence": 0x2E,
"cement": 0x2F, "combustion": 0x2F,
"chairlift": 0x30, "commando": 0x30,
"chatter": 0x31, "company": 0x31,
"checkup": 0x32, "component": 0x32,
"chisel": 0x33, "concurrent": 0x33,
"choking": 0x34, "confidence": 0x34,
"chopper": 0x35, "conformist": 0x35,
"Christmas": 0x36, "congregate": 0x36,
"clamshell": 0x37, "consensus": 0x37,
"classic": 0x38, "consulting": 0x38,
"classroom": 0x39, "corporate": 0x39,
"cleanup": 0x3A, "corrosion": 0x3A,
"clockwork": 0x3B, "councilman": 0x3B,
"cobra": 0x3C, "crossover": 0x3C,
"commence": 0x3D, "crucifix": 0x3D,
"concert": 0x3E, "cumbersome": 0x3E,
"cowbell": 0x3F, "customer": 0x3F,
"crackdown": 0x40, "Dakota": 0x40,
"cranky": 0x41, "decadence": 0x41,
"crowfoot": 0x42, "December": 0x42,
"crucial": 0x43, "decimal": 0x43,
"crumpled": 0x44, "designing": 0x44,
"crusade": 0x45, "detector": 0x45,
"cubic": 0x46, "detergent": 0x46,
"dashboard": 0x47, "determine": 0x47,
"deadbolt": 0x48, "dictator": 0x48,
"deckhand": 0x49, "dinosaur": 0x49,
"dogsled": 0x4A, "direction": 0x4A,
"dragnet": 0x4B, "disable": 0x4B,
"drainage": 0x4C, "disbelief": 0x4C,
"dreadful": 0x4D, "disruptive": 0x4D,
"drifter": 0x4E, "distortion": 0x4E,
"dropper": 0x4F, "document": 0x4F,
"drumbeat": 0x50, "embezzle": 0x50,
"drunken": 0x51, "enchanting": 0x51,
"Dupont": 0x52, "enrollment": 0x52,
"dwelling": 0x53, "enterprise": 0x53,
"eating": 0x54, "equation": 0x54,
"edict": 0x55, "equipment": 0x55,
"egghead": 0x56, "escapade": 0x56,
"eightball": 0x57, "Eskimo": 0x57,
"endorse": 0x58, "everyday": 0x58,
"endow": 0x59, "examine": 0x59,
"enlist": 0x5A, "existence": 0x5A,
"erase": 0x5B, "exodus": 0x5B,
"escape": 0x5C, "fascinate": 0x5C,
"exceed": 0x5D, "filament": 0x5D,
"eyeglass": 0x5E, "finicky": 0x5E,
"eyetooth": 0x5F, "forever": 0x5F,
"facial": 0x60, "fortitude": 0x60,
"fallout": 0x61, "frequency": 0x61,
"flagpole": 0x62, "gadgetry": 0x62,
"flatfoot": 0x63, "Galveston": 0x63,
"flytrap": 0x64, "getaway": 0x64,
"fracture": 0x65, "glossary": 0x65,
"framework": 0x66, "gossamer": 0x66,
"freedom": 0x67, "graduate": 0x67,
"frighten": 0x68, "gravity": 0x68,
"gazelle": 0x69, "guitarist": 0x69,
"Geiger": 0x6A, "hamburger": 0x6A,
"glitter": 0x6B, "Hamilton": 0x6B,
"glucose": 0x6C, "handiwork": 0x6C,
"goggles": 0x6D, "hazardous": 0x6D,
"goldfish": 0x6E, "headwaters": 0x6E,
"gremlin": 0x6F, "hemisphere": 0x6F,
"guidance": 0x70, "hesitate": 0x70,
"hamlet": 0x71, "hideaway": 0x71,
"highchair": 0x72, "holiness": 0x72,
"hockey": 0x73, "hurricane": 0x73,
"indoors": 0x74, "hydraulic": 0x74,
"indulge": 0x75, "impartial": 0x75,
"inverse": 0x76, "impetus": 0x76,
"involve": 0x77, "inception": 0x77,
"island": 0x78, "indigo": 0x78,
"jawbone": 0x79, "inertia": 0x79,
"keyboard": 0x7A, "infancy": 0x7A,
"kickoff": 0x7B, "inferno": 0x7B,
"kiwi": 0x7C, "informant": 0x7C,
"klaxon": 0x7D, "insincere": 0x7D,
"locale": 0x7E, "insurgent": 0x7E,
"lockup": 0x7F, "integrate": 0x7F
}
def decode_flag(encoded_words):
decoded_hex = []
for word in encoded_words:
if word in word_list:
decoded_hex.append(hex(word_list[word])[2:])
else:
print(f"未找到单词: {word}")
return None
decoded_hex_str = ''.join(decoded_hex)
decoded_bytes = bytes.fromhex(decoded_hex_str)
return decoded_bytes.decode('utf-8', errors='ignore')
encoded_words = [
"crumpled","chairlift","freedom","chisel","island","dashboard","crucial","kickoff","crucial","chairlift","drifter","classroom","highchair","cranky","clamshell","edict","drainage","fallout","clamshell","chatter","chairlift","goldfish","chopper","eyetooth","endow","chairlift","edict","eyetooth","deadbolt","fallout","egghead","chisel","eyetooth","cranky","crucial","deadbolt","chatter","chisel","egghead","chisel","crumpled","eyetooth","clamshell","deadbolt","chatter","chopper","eyetooth","classroom","chairlift","fallout","drainage","klaxon"
]
flag = decode_flag(encoded_words)
if flag:
print(flag)
- 标题: 国城杯wp
- 作者: moshui
- 创建于 : 2024-12-07 12:12:37
- 更新于 : 2024-12-07 19:17:07
- 链接: https://www.moshui.eu.org/2024/12/07/guochengCup/
- 版权声明: 本文章采用 CC BY-NC-SA 4.0 进行许可。